Block-IPsPerCountry function added to AZSBTools PowerShell Module to bring GeoIP filtering to the Windows firewall
In prior posts I outlined AZSBTools PowerShell module functions to:
- Search Windows Security and RdpCoreTS (Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational) event logs for Failure Audit events (Event IDs 4625, 5061, 140).
Report-FailureAudit function is described in this post. - Provide summary report on data returned from Report-FailureAudit function. Summarize-FailureAudit function is also described in this post.
- Backup one or more Windows Event Logs and clear one or more Windows Event Logs. Backup-EventLog and Clear-SBEventLog functions are described in the post.
- Add Windows firewall rules to block a provided list of IPv4 addresses or CIDR subnets. Update-WindowsFirewall function is also described in this post.
As described in this post, these functions can be used together to provide an automation to mitigate against brute force attempts to crack a Windows computer account password by detecting failed login attempts from Windows event logs, report and aggregate the results, and create Windows firewall rules to block access from the attacking IPs.
However, practice shows that attackers often use botnets to do this sort of attack. Here’s an example of part of a log file of the Block-FailedLogonIPs PowerShell automation (scheduled task) described in this post:
10 October 2021 05:52:09 AM: Reading Security Event Log on computer mycomp1 10 October 2021 05:52:22 AM: .. read 2043 events in 0:0:13 (hh:mm:ss) 10 October 2021 05:52:22 AM: Reading 'RdpCoreTS/Operational' Event Log on computer mycomp1 10 October 2021 05:52:22 AM: .. read 137 events in 0:0:0 (hh:mm:ss) 10 October 2021 05:52:23 AM: Reading 'SQL/Application' Event Log on computer mycomp1 10 October 2021 05:52:23 AM: No FailureAudit events found in Application Event Log for computer mycomp1 10 October 2021 05:52:23 AM: Processing Security Log events 4625 and 5061 on computer mycomp1 10 October 2021 05:52:43 AM: .. done in 0:0:20 (hh:mm:ss) 10 October 2021 05:52:43 AM: Processing 'RdpCoreTS/Operational' Log events 139/140 on computer mycomp1 10 October 2021 05:52:43 AM: .. done in 0:0:0 (hh:mm:ss) 10 October 2021 05:52:43 AM: No events of type FailureAudit found in the Windows Application EventLog 10 October 2021 05:52:43 AM: Processing summary report 10 October 2021 05:52:43 AM: Security Event summary: 10 October 2021 05:52:43 AM: EventCount : 2,043 FirstEventTime : 10/10/2021 5:18:29 AM LastEventTime : 10/10/2021 5:52:07 AM Duration : 0:0:33:37 (dd:hh:mm:ss) AttemptsPerHour : 3,645 AttemptsLastHour : 2,043 EventLog : Security EventType : Audit Failure EventId : 4625 10 October 2021 05:52:43 AM: Security Event summary exported to .\Reports\Summarize-FailureAudit_PerLog_Security_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:44 AM: No Failure Audit Events found in RdpCoreTS event log 10 October 2021 05:52:44 AM: No Failure Audit Events found in Application event log 10 October 2021 05:52:44 AM: Source IP summary (Top 10): 10 October 2021 05:52:44 AM: IPAddress : 94.232.47.56 ReverseDNS : IPLocation : Moscow, Moscow, 127224 - RU (55.7522,37.6156) IPOrg : AS204490 Kontel LLC IPTimeZone : Europe/Moscow AttemptCount : 1045 Percent : 47.94 % IPAddress : 94.232.47.57 ReverseDNS : IPLocation : Moscow, Moscow, 127224 - RU (55.7522,37.6156) IPOrg : AS204490 Kontel LLC IPTimeZone : Europe/Moscow AttemptCount : 1038 Percent : 47.61 % IPAddress : 193.93.62.80 ReverseDNS : IPLocation : Riga, Riga, LV-1001 - LV (56.9460,24.1059) IPOrg : AS39814 SIA IT Services IPTimeZone : Europe/Riga AttemptCount : 45 Percent : 2.06 % IPAddress : 193.93.62.72 ReverseDNS : IPLocation : IPOrg : IPTimeZone : AttemptCount : 37 Percent : 1.70 % IPAddress : 193.93.62.84 ReverseDNS : IPLocation : IPOrg : IPTimeZone : AttemptCount : 15 Percent : 0.69 % 10 October 2021 05:52:44 AM: Source IP summary exported to .\Reports\Summarize-FailureAudit_PerSourceIP_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:44 AM: Logon Attempt Type summary (Top 10): 10 October 2021 05:52:44 AM: LogonType AttemptCount Percent --------- ------------ ------- Network 2180 100.00 % 10 October 2021 05:52:44 AM: Logon Type summary exported to .\Reports\Summarize-FailureAudit_PerLogonType_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:45 AM: Attempted Account summary (Top 10): 10 October 2021 05:52:45 AM: Account AttemptCount Percent ------- ------------ ------- Not reported in event 140 137 6.28 % \ADMINISTRATOR 90 4.13 % \energyprz 1 0.05 % \drkulas 1 0.05 % \fontaine 1 0.05 % \dreamlines 1 0.05 % \fatlab 1 0.05 % \docuprint 1 0.05 % \g2is 1 0.05 % \energychaser 1 0.05 % 10 October 2021 05:52:46 AM: User Name summary exported to .\Reports\Summarize-FailureAudit_PerUserName_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:46 AM: All records exported to .\Reports\Summarize-FailureAudit_All_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:46 AM: Latest 10 attempts: 10 October 2021 05:52:46 AM: EventID ComputerName LogName Account SourceIP TimeCreated ------- ------------ ------- ------- -------- ----------- 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:20 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:20 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:18 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:17 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:16 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:16 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:14 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:13 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:12 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:11 AM
This log file and numerous similar logs show:
- Incoming attempts; mostly from Russia; to guess (mostly) ‘Administrator’ account password on Windows computers that are listening for RDP (Remote Desktop Protocol) connections.
- The attackers’ automation is able to recognize which of their sender nodes are blocked and use other unblocked nodes to continue the same attack.
- The Windows firewall rules can block a maximum of 10k IPs/CIDR subnets per rule.
So if the Block-FailedLogonIPs PowerShell automation is scheduled hourly, it detects and blocks the attacker IPs for the prior hour. However, the next hour IPs are different. The attacker does not seem to run out of IPs, or to have a Botnet with larger than 10k nodes. This solution essentially fails at its intended purpose of blocking unauthorized RDP connections. It, however, has the unanticipated side result of building a database of thousands of the attacker IPs.
This new function Block-IPsPerCountry takes a different approach to the same problem. It leverages GeoIP information (courtesy of ipdeny.com) to create firewall rules to block all incoming IP traffic except a given 1 or more countries.
Example:
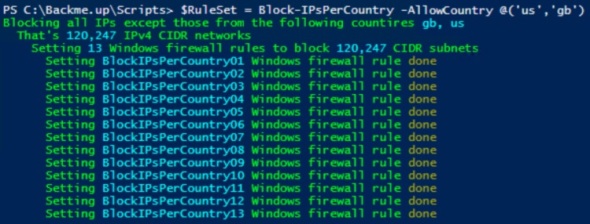
$RuleSet = Block-IPsPerCountry -AllowCountry @('us','gb')
This may take several minutes to complete. This example blocks all incoming IPv4 traffic except from USA or Great Britain. Console output looks like:
ISO Alpha-2 country code list can be seen here.
Continuing to use Block-FailedLogonIPs PowerShell automation as an hourly scheduled task shows no more incoming attempts to crack Administrator password via repeated RDP logon attempts.
To use/update the AZSBTools PowerShell module which is available in the PowerShell Gallery, you can use the following code:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
# PowerShellGallery dropped Ssl3 and Tls as of 1 April 2020
Remove-Module AZSBTools -Force -EA 0
Install-Module AZSBTools -Force -AllowClobber -SkipPublisherCheck # -Scope CurrentUser
Import-Module AZSBTools -DisableNameChecking -Force
Get-Command -Module AZSBTools
You need PowerShell 5. To view your PowerShell version, in an elevated PowerShell ISE window type
$PSVersionTable
To download and install the latest version of AZSBTools from the PowerShell Gallery and its dependencies, type
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
To trust the Microsoft PowerShell Gallery repository, then
Install-Module AZSBTools,Az -Force -AllowClobber -Scope CurrentUser
AZSBTools contains functions that depend on Az module, and they’re typically installed together.
To load the AZSBTools, and Az modules type:
Import-Module AZSBTools,Az -DisableNameChecking
To view a list of cmdlets/functions in AZSBTools, type
Get-Command -Module AZSBTools
To view the built-in help of one of the AZSBTools functions/cmdlets, type
help <function/cmdlet name> -show
such as
help Get-DayOfMonth -show
Cleanup-WindowsFolder function added to AzSBTools PowerShell module
The Windows folder can sometimes grow to several dozen gigabytes as the new Windows updates and Service Packs pile up over time. To reduce that space, Microsoft offers several options outlined in this document. This Cleanup-WindowsFolder function automates these options. It offers 4 levels of cleanup:
Level 0
This is the default level. It cleans up temporary files in the Windows Font Cache folder. These are files with the ‘Temporary’ attribute, typically under the ‘C:\Windows\ServiceProfiles\LocalService\AppData\Local’ folder. In an active system this can add up to many gigabytes of space.

Level 1
This is the least aggressive level that invokes DISM. It invokes the following DISM command:
Dism.exe /online /Cleanup-Image /StartComponentCleanup

Level 2
This can be invoked as follows:
Cleanup-WindowsFolder -Level 2
Which will invoke the command:
Dism.exe /online /Cleanup-Image /StartComponentCleanup /ResetBase
Which will delete older unused components and safely cleanup c:\Windows\WinSXS (No 30 day grace period), AND remove all superseded versions of every component in the component store. (All existing service packs and updates cannot be uninstalled)
Level 3
This is the most aggressive level. In addition to all cleanup performed by level 2, it also invokes
Dism.exe /online /Cleanup-Image /SPSuperseded
Which removes any backup components needed for uninstallation of the service pack. Service packs cannot be uninstalled after this command is completed.
This function requires elevation.
If DISM fails, this function will report it:

This particular issue can be resolved by restarting the computer.
To use/update the AZSBTools PowerShell module which is available in the PowerShell Gallery, you can use the following code:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
# PowerShellGallery dropped Ssl3 and Tls as of 1 April 2020
Remove-Module AZSBTools -Force -EA 0
Install-Module AZSBTools -Force -AllowClobber -SkipPublisherCheck # -Scope CurrentUser
Import-Module AZSBTools -DisableNameChecking -Force
Get-Command -Module AZSBTools
You need PowerShell 5. To view your PowerShell version, in an elevated PowerShell ISE window type
$PSVersionTable
To download and install the latest version of AZSBTools from the PowerShell Gallery and its dependencies, type
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
To trust the Microsoft PowerShell Gallery repository, then
Install-Module AZSBTools,Az -Force -AllowClobber -Scope CurrentUser
AZSBTools contains functions that depend on Az module, and they’re typically installed together.
To load the AZSBTools, and Az modules type:
Import-Module AZSBTools,Az -DisableNameChecking
To view a list of cmdlets/functions in AZSBTools, type
Get-Command -Module AZSBTools
To view the built-in help of one of the AZSBTools functions/cmdlets, type
help <function/cmdlet name> -show
such as
help Get-DayOfMonth -show
New-BlockList function added to AZSBTools PowerShell module
Windows firewall rules are not evaluated in order like most firewalls. They also don’t offer a scope option such as “All IPs except…”.
So to block one or more IPs, you have to list them. That list can be in the format of a single IPv4 address like 1.2.3.4, a CIDR range like 1.2.3.0/24, or a simple range like 1.2.3.4-2.3.4.5
In many use cases, we want to block all IPs except a small list of authorized IPs or IP CIDR ranges. This function facilitates this task by creating simple IP ranges that cover the entire IPv4 address space excet the provided list of IPs/CIDR ranges.
This function takes one parameter; AllowedIP which takes one or more IPv4 addresses or CIDR ranges.
Example:
New-BlockList -AllowedIP @( '99.88.77.66' '33.44.55.111' )
This returns output like:
1.0.0.1-33.44.55.110 33.44.55.112-99.88.77.65 99.88.77.67-255.255.255.255
This output can be used to configure a Windows Firewall rule to block all IPs except the two listed in the AllowedIP parameter as in:
Remove-NetFirewallRule -Name 'Allow authorized IPs only' -Confirm:$false -EA 0 $ParameterSet = @{ RemoteAddress = New-BlockList -AllowedIP @( '99.88.77.66' '33.44.55.111' ) Direction = 'Inbound' Profile = 'Any' Action = 'Block' Enabled = 'True' Name = 'Allow authorized IPs only' DisplayName = 'Allow authorized IPs only' Description = 'Allow authorized IPs only' } New-NetFirewallRule @ParameterSet
We can also use CIDR ranges, private IP addresses/ranges and DNS names as in:
New-BlockList -AllowedIP @( (Resolve-DnsName -Name goodsite.com -Type A).IPAddress '99.88.77.66' '33.44.55.111' '192.168.11.0/24' '10.0.0.0/12' '66.77.88.48/29' )
Here goodsite.com resolves to
121.254.178.253
and the output would look like:
1.0.0.1-9.255.255.255 10.16.0.0-33.44.55.110 33.44.55.112-66.77.88.47 66.77.88.56-99.88.77.65 99.88.77.67-121.254.178.252 121.254.178.254-192.168.10.255 192.168.12.0-255.255.255.255
To use/update the AZSBTools PowerShell module which is available in the PowerShell Gallery, you can use the following code:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
# PowerShellGallery dropped Ssl3 and Tls as of 1 April 2020
Remove-Module AZSBTools -Force -EA 0
Install-Module AZSBTools -Force -AllowClobber -SkipPublisherCheck # -Scope CurrentUser
Import-Module AZSBTools -DisableNameChecking -Force
Get-Command -Module AZSBTools
You need PowerShell 5. To view your PowerShell version, in an elevated PowerShell ISE window type
$PSVersionTable
To download and install the latest version of AZSBTools from the PowerShell Gallery and its dependencies, type
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
To trust the Microsoft PowerShell Gallery repository, then
Install-Module AZSBTools,Az -Force -AllowClobber -Scope CurrentUser
AZSBTools contains functions that depend on Az module, and they’re typically installed together.
To load the AZSBTools, and Az modules type:
Import-Module AZSBTools,Az -DisableNameChecking
To view a list of cmdlets/functions in AZSBTools, type
Get-Command -Module AZSBTools
To view the built-in help of one of the AZSBTools functions/cmdlets, type
help <function/cmdlet name> -show
such as
help Get-DayOfMonth -show
Powershell 5
Powershell 5 is expected to be released with Windows 10. It’s currently (April 2015) in preview. It’s backward compatible with Windows 8, 8.1, 2012, and 2012 R2. To get PS5 install WMF5 from this link. Here’s the general PowershellGet architecture:
For more information see the Powershell Gallery. PS5 installation requires a reboot
 After a reboot, in Powershell ISE, PS version shows as version 5
After a reboot, in Powershell ISE, PS version shows as version 5
$PSVersionTable
 PS5 comes with PowershellGet module. To see its commands:
PS5 comes with PowershellGet module. To see its commands:
Get-Command -Module PowerShellGet
When running for the first time, run this command to automate the download of the needed nuget-anycpu.exe
Get-PackageProvider -Name NuGet -ForceBootstrap
 The default Repository is the Powershell Gallery, and it’s untrusted by default:
The default Repository is the Powershell Gallery, and it’s untrusted by default:
 To check out currently available modules:
To check out currently available modules:
$Modules = Find-Module
$Modules.Count # 153
$Modules | sort name | select * | Out-GridView
To install a module from the Gallery, use Install-Module as in:
Install-Module Pester
 Since the Powershell Gallery is untrusted by default, we’ll get the message above. If you want to trust the Powershell Gallery, use:
Since the Powershell Gallery is untrusted by default, we’ll get the message above. If you want to trust the Powershell Gallery, use:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
Alternatively, use the -Force parameter with the Install-Module command to avoid the untrusted repository prompt.
Pester is a great unit testing module to help test Powershell scripts, developed by David Wyatt and the Pester team. To see its commands:
Get-Command -Module Pester
For more information on Pester see Pester on GitHub and video presentation from Powershell Summit NA 2015.
Now I have this module and can use its commands.
One of the great benefits of a NuGet repository for PS modules like PowershellGet is version control, as it keeps track of module versions as they’re published. To see different versions of a module:
Find-Module -Name Pester -AllVersions | select version,PublishedDate | FT -a
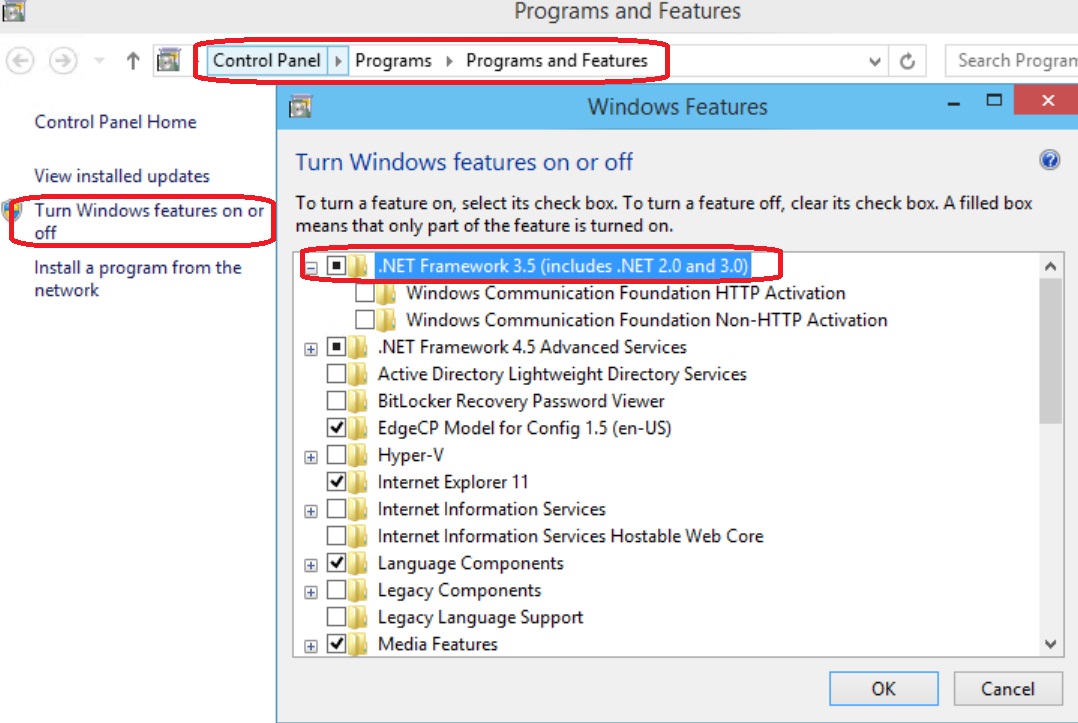
DOT NET 3.5 for Windows 10 Technical Preview
DOT NET 3.5 was often hard to install on Windows 8, 8.1, 2012, and 2012 R2. I tested installing it on Windows 10 Technical Preview for Enterprise:
In Control Panel\Programs\Programs and Features, click turn Windows features on or off, and check the “.NET Framework 3.5” box and click OK
Click “Download files from Windows Update”
It just works!
Same can be done via the DISM command line utility:
DISM /Online /Enable-Feature /FeatureName:NetFx3 /All
Again it works just fine!
Using SysPrep with Windows 10 Technical Preview for Enterprise
SysPrep.exe is a tool located under c:\windows\system32\SysPrep folder. It can be used to “generalize” a Windows installation to be used for automated deployment instead of doing every fresh install from the ISO media.
After doing a fresh install of Windows 10 Technical Preview for Enterprise as a Gen 2 VM on Server 2012 R2 Hyper-V host, I ran Windows updates, enabled Remote Desktop, installed 2 Windows updates updates, rebooted, installed RSAT, then I ran SysPrep.exe
I chose to “Generalize” and “Shutdown”, so that I can copy the VM’s VHDX file to be used for other Windows 10 Technical Preview machine deployments.
Sysprep will prepare the system and shutdown the computer.
After copying the VHDX file, I restarted the VM:
Set Region and Language, accept license agreement, skip product key:
Although the product key was skipped, later on after the machine was setup and rebooted, Windows auto-activated. No need to enter a product key or manually activate:
Windows 10 Technical Preview and Windows 10 Technical Preview for Enterprise license expires April 15, 2015.
Enter a user name and password:
Notes:
- Do NOT join the domain prior to running Sysprep. It will fail with “Fatal error” similar to this:

- Currently Sysprep does not let you use a local account that was setup prior to running SysPrep. You will have to setup another local account when using the SysPrep’d image
- Local Administrator account is disabled by default on Windows 10 Technical Preview
Remote Server Administration Tools (RSAT) for Windows 10 Technical Preview
Remote Server Administration Tools (RSAT) for Windows 10 Technical Preview are now available for download. Download and install the version that matches your Windows 10 installation (x86 or x64)
I wanted to know what Powershell modules this will add to a fresh Windows 10 Technical Preview for Enterprise. So I used this short script:
Get-Module -ListAvailable | Select name,version,ModuleType,ClrVersion,PowershellVersion | Export-Csv .\Win10b-modules.csv -NoTypeInformation # Install RSAT tools for Windows 10 Technical Preview # http://www.microsoft.com/en-us/download/details.aspx?id=44280 .\WindowsTH-KB2693643-x64.msu Get-Module -ListAvailable | Select name,version,ModuleType,ClrVersion,PowershellVersion | Export-Csv .\Win10c-modules.csv -NoTypeInformation Compare-Object -ReferenceObject (Import-Csv .\Win10b-modules.csv).name ` -DifferenceObject (Import-Csv .\Win10c-modules.csv).name
The first 3 lines save a list of the installed PS modules in a CSV file.
Next I installed RSAT:
then accepted the license agreement.
Installation finished successfully. This added shortcuts to Server Manager tool (c:\windows\system32\ServerManager.exe) on the start menu and under All Apps
A comparison of the PS module before and after the installation showed that RSAT added the following 19 modules:
ActiveDirectory
ClusterAwareUpdating
DFSN
DFSR
DhcpServer
DnsServer
FailoverClusters
GroupPolicy
IpamServer
IscsiTarget
NetworkController
NetworkLoadBalancingClusters
NFS
RemoteDesktop
ServerManager
ServerManagerTasks
StorageQoS
UpdateServices
WVR
If you encounter errors with Sysprep see this KB article. It’s for Windows 8 but it applies to Windows 10 Technical Preview as well.
1/8/2015 – Window Technical Preview build 9879:
Some may have access to the new Windows Technical Preview build 9879 available in the MSDN subscription secure download site.
I’ve done a fresh install of Windows Technical Preview build 9879, and attempted to install RSAT normally. That just worked:
In another fresh install of WinTP 9879 I tried using DISM:
That completed successfully as well.
Some have reported errors attempting to install RSAT for Windows TP. I’ve downloaded the latest Windows TP ISO and did a fresh install as a Gen 2 virtual machine on Hyper-V 2012 R2. I downloaded and installed RSAT without any issue. I wan not able to replicate the problem. However, here’s another way to try to install it:
Download the WindowsTH-KB2693643-x64.msu file as usual – save it to the default location under ‘downloads’
Run the following script in Powershell_ISE (as administrator – elevated permissions)
$Path = "$env:USERPROFILE\downloads\WindowsTH-KB2693643-x64.msu"
# Exctract .cab file $Target = "$env:USERPROFILE\downloads\RSAT" wusa.exe $Path /extract:$Target
# Install via DISM $CAB = "$env:USERPROFILE\downloads\RSAT\WindowsTH-KB2693643-x64.cab" Dism.exe /Online /Add-Package /PackagePath:$CAB
Windows 10 Technical Preview for Enterprise updates
On 10/2/2014 I ran Windows Updates on a plain vanilla installation of Windows 10 Technical Preview for Enterprise. It found 1 update:
I installed, and rebooted
It took a little longer than expected for a Gen 2 VM. After reboot, I looked for installed updates, and found 2 (!):
The first update is KB3001512 which addresses these issues:
- In Windows Technical Preview, certain devices do not receive firmware or driver updates.
- Adobe Flash update does not contain premium video playback.
- Some problems in the Compatibility View list for Internet Explorer 11
The second update is KB3002675. Powershell shows that its information link is http://support.microsoft.com/?kbid=3002675 but this seems to be a broken link at this time..
Windows 10 Technical Preview – Hyper-V Integration
After installing Windows 10 Technical Preview on Windows Server 2012 R2, I checked the integration service. In Hyper-V Manager on the 2012 R2 host, all looked normal:
Running the following Powershell command on the 2012 R2 Hyper-V server showed that the Windows 10 Technical Preview VM comes with Integration Service version 6.4.9841
This command shows more details:
Running this comparison between Integration services for the this Windows 10 VM and a Server 2012 R2 VM:
Compare-Object -ReferenceObject (Get-VMIntegrationService -VMName v-Win10a | select *) -DifferenceObject (Get-VMIntegrationService -VMName v-2012R2-G2a | select *)
showed no difference (This does not show or compare integration service version.)
Windows 10 Technical Preview – early look at Windows components and features
Checking versions of different Windows components in Windows 10 Technical Preview:
It comes with Powershell 5 !!
Looking at the OS version, it is version 6.4.9841.0
 This is shown from WMI, and on file versions, and help/about:
This is shown from WMI, and on file versions, and help/about:
Navigation is almost identical to Windows 8.1/Server 2012 R2, which I find very comforting.
Checking the available Powershell modules with the command:
Get-Module -ListAvailable | Select name,version,ModuleType,ClrVersion,PowershellVersion | Export-Csv .\Win10-modules.csv -NoTypeInformation
Shows the following 62 modules:
| Name | Version | ModuleType | ClrVersion | PowerShellVersion |
| AppBackgroundTask | 1.0.0.0 | Manifest | 3 | |
| AppLocker | 2.0.0.0 | Manifest | 4 | 3 |
| Appx | 2.0.0.0 | Manifest | 4 | 3 |
| AssignedAccess | 1.0.0.0 | Script | ||
| BitLocker | 1.0.0.0 | Manifest | 4 | 3 |
| BitsTransfer | 2.0.0.0 | Manifest | 4 | 3 |
| BranchCache | 1.0.0.0 | Manifest | 3 | |
| CimCmdlets | 1.0.0.0 | Manifest | 4 | 3 |
| Defender | 1 | Manifest | 3 | |
| DirectAccessClientComponents | 1.0.0.0 | Manifest | 3 | |
| Dism | 3 | Script | 4 | 4 |
| DnsClient | 1.0.0.0 | Manifest | 4 | 3 |
| International | 2.0.0.0 | Manifest | 4 | 3 |
| iSCSI | 1.0.0.0 | Manifest | 3 | |
| ISE | 1.0.0.0 | Script | 4 | 3 |
| Kds | 1.0.0.0 | Manifest | 4 | 3 |
| Microsoft.PowerShell.Archive | 1.0.0.0 | Manifest | ||
| Microsoft.PowerShell.Diagnostics | 3.0.0.0 | Manifest | 4 | 3 |
| Microsoft.PowerShell.Host | 3.0.0.0 | Manifest | 4 | 3 |
| Microsoft.PowerShell.Management | 3.1.0.0 | Manifest | 4 | 3 |
| Microsoft.PowerShell.ODataUtils | 1 | Script | ||
| Microsoft.PowerShell.Security | 3.0.0.0 | Manifest | 4 | 3 |
| Microsoft.PowerShell.Utility | 3.1.0.0 | Manifest | 4 | 3 |
| Microsoft.WSMan.Management | 3.0.0.0 | Manifest | 4 | 3 |
| MMAgent | 1 | Manifest | 3 | |
| MsDtc | 1.0.0.0 | Manifest | 4 | 3 |
| NetAdapter | 2.0.0.0 | Manifest | 3 | |
| NetConnection | 1.0.0.0 | Manifest | 3 | |
| NetEventPacketCapture | 1.0.0.0 | Manifest | 3 | |
| NetLbfo | 2.0.0.0 | Manifest | 3 | |
| NetNat | 1.0.0.0 | Manifest | 3 | |
| NetQos | 2.0.0.0 | Manifest | 3 | |
| NetSecurity | 2.0.0.0 | Manifest | 4 | 3 |
| NetSwitchTeam | 1.0.0.0 | Manifest | 3 | |
| NetTCPIP | 1.0.0.0 | Manifest | 3 | |
| NetworkConnectivityStatus | 1.0.0.0 | Manifest | 3 | |
| NetworkSwitch | 1.0.0.0 | Script | 3 | |
| NetworkTransition | 1.0.0.0 | Manifest | 3 | |
| OneGet | 1.0.0.0 | Binary | 4 | 2 |
| PcsvDevice | 1.0.0.0 | Manifest | 3 | |
| PKI | 1.0.0.0 | Manifest | 4 | 3 |
| PowerShellGet | 0.5 | Script | 3 | |
| PrintManagement | 1.1 | Manifest | 3 | |
| PSDesiredStateConfiguration | 1 | Manifest | ||
| PSDiagnostics | 1.0.0.0 | Script | 2.0.50727 | 2 |
| PSScheduledJob | 1.1.0.0 | Binary | 4 | 3 |
| PSWorkflow | 2.0.0.0 | Manifest | 4 | 3 |
| PSWorkflowUtility | 1.0.0.0 | Manifest | 4 | 3 |
| ScheduledTasks | 1.0.0.0 | Manifest | 4 | 3 |
| SecureBoot | 2.0.0.0 | Manifest | 4 | 3 |
| SmbShare | 2.0.0.0 | Manifest | 3 | |
| SmbWitness | 2.0.0.0 | Manifest | 3 | |
| StartScreen | 1.0.0.0 | Manifest | 4 | 3 |
| Storage | 2.0.0.0 | Manifest | 3 | |
| TLS | 2.0.0.0 | Manifest | 4 | 3 |
| TroubleshootingPack | 1.0.0.0 | Manifest | 4 | 3 |
| TrustedPlatformModule | 2.0.0.0 | Manifest | 4 | 3 |
| VpnClient | 2.0.0.0 | Manifest | 3 | |
| Wdac | 1.0.0.0 | Manifest | 3 | |
| WindowsDeveloperLicense | 1.0.0.0 | Manifest | 4 | 3 |
| WindowsErrorReporting | 1 | Script | 4 | 3 |
| WindowsSearch | 1.0.0.0 | Manifest | 4 | 3 |
I ran the same command on a Windows 2012 R2 server (that has Powershell 4) and ran a comparison:
Compare-Object -ReferenceObject (Import-Csv .\Win8-modules.csv).name `
-DifferenceObject (Import-Csv .\Win10-modules.csv).name
That showed the following 8 new modules:
AppBackgroundTask AssignedAccess Defender Microsoft.PowerShell.Archive Microsoft.PowerShell.ODataUtils NetworkSwitch OneGet PowerShellGet
Windows 10 Technical Preview – early look at the user interface
Just installed Windows 10 Technical Preview as a Gen 2 VM on Server 2012 R2 Hyper-V. Here’s what we know:
It comes with IE 11:
The start menu looks like a combo of Windows 7 and Windows 8 tile:
I pinned the Powershell icons to the task bar, they were not there before..
Clicking on the logged on name on top bring up 3 options:
Trying the “Change account picture”:
I browsed to a picture and selected it. The browse dialog box defaulted to the Pictures folder:
The Lock option worked as expected:
By default it brought on the on screen keyboard..
The Sign out option had an error:
 Sign out anyway option worked, and I was signed out.
Sign out anyway option worked, and I was signed out.
If you click All Apps at the bottom of the start menu you see:
Trying the search field:
I clicked Computer Management link on top expecting to get this:
but instead I got a Bing search:
I was able to get to the Computer Management tool via right-clicking on “This PC” in File Explorer and choosing Manage:
It seems anything you search for in the “Search Anywhere” box simply brings a Bing search..
Installing Windows 10 Technical Preview as Gen 2 VM on Hyper-V 2012 R2
 Microsoft released Windows 10 Technical Preview today 10/1/2014 shortly after noon time. Here’s how the installation went:
Microsoft released Windows 10 Technical Preview today 10/1/2014 shortly after noon time. Here’s how the installation went:
Media: ISO file:
Setup: Gen 2 VM on Server 2012 R2 hypevisor, 50 GB disk, mounted the iso, 2 GB startup dynamic RAM, 1 GB minimum, 8 GB maximum, 4 cores.
After a reboot, this screen came up:
And, of course, I clicked “Customize”
I went with “Yes”
These are the default settings. For this test, I’m accepting all defaults
I’m pleasantly surprised that these are the defaults!
I did not like those much..
 The familiar “Checking your Internet connection” message
The familiar “Checking your Internet connection” message
I had DHCP turned off on the network, so the VM did not pick up an IP address and could not connect to the Internet automatically. This is what I wanted. So, I clicked “Create a local account”
A Password hint is required.
and the familiar “Finalizing your settings” message..
and the desktop appeared. Installation is complete!
No key or license was needed.
That was quick and painless. No crash, no blue screen, no surprise. So far so good!!
I entered an IP address and was connected to the network and the Internet:
And the OS version was:
10/2/2014:
I got a copy of the ISO for Windows 10 Technical Preview for Enterprise:
Installation was identical to the above. I cannot see any differences from the version above. Both seem to be the Client OS version of Windows 10