Block-IPsPerCountry function added to AZSBTools PowerShell Module to bring GeoIP filtering to the Windows firewall
In prior posts I outlined AZSBTools PowerShell module functions to:
- Search Windows Security and RdpCoreTS (Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational) event logs for Failure Audit events (Event IDs 4625, 5061, 140).
Report-FailureAudit function is described in this post. - Provide summary report on data returned from Report-FailureAudit function. Summarize-FailureAudit function is also described in this post.
- Backup one or more Windows Event Logs and clear one or more Windows Event Logs. Backup-EventLog and Clear-SBEventLog functions are described in the post.
- Add Windows firewall rules to block a provided list of IPv4 addresses or CIDR subnets. Update-WindowsFirewall function is also described in this post.
As described in this post, these functions can be used together to provide an automation to mitigate against brute force attempts to crack a Windows computer account password by detecting failed login attempts from Windows event logs, report and aggregate the results, and create Windows firewall rules to block access from the attacking IPs.
However, practice shows that attackers often use botnets to do this sort of attack. Here’s an example of part of a log file of the Block-FailedLogonIPs PowerShell automation (scheduled task) described in this post:
10 October 2021 05:52:09 AM: Reading Security Event Log on computer mycomp1 10 October 2021 05:52:22 AM: .. read 2043 events in 0:0:13 (hh:mm:ss) 10 October 2021 05:52:22 AM: Reading 'RdpCoreTS/Operational' Event Log on computer mycomp1 10 October 2021 05:52:22 AM: .. read 137 events in 0:0:0 (hh:mm:ss) 10 October 2021 05:52:23 AM: Reading 'SQL/Application' Event Log on computer mycomp1 10 October 2021 05:52:23 AM: No FailureAudit events found in Application Event Log for computer mycomp1 10 October 2021 05:52:23 AM: Processing Security Log events 4625 and 5061 on computer mycomp1 10 October 2021 05:52:43 AM: .. done in 0:0:20 (hh:mm:ss) 10 October 2021 05:52:43 AM: Processing 'RdpCoreTS/Operational' Log events 139/140 on computer mycomp1 10 October 2021 05:52:43 AM: .. done in 0:0:0 (hh:mm:ss) 10 October 2021 05:52:43 AM: No events of type FailureAudit found in the Windows Application EventLog 10 October 2021 05:52:43 AM: Processing summary report 10 October 2021 05:52:43 AM: Security Event summary: 10 October 2021 05:52:43 AM: EventCount : 2,043 FirstEventTime : 10/10/2021 5:18:29 AM LastEventTime : 10/10/2021 5:52:07 AM Duration : 0:0:33:37 (dd:hh:mm:ss) AttemptsPerHour : 3,645 AttemptsLastHour : 2,043 EventLog : Security EventType : Audit Failure EventId : 4625 10 October 2021 05:52:43 AM: Security Event summary exported to .\Reports\Summarize-FailureAudit_PerLog_Security_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:44 AM: No Failure Audit Events found in RdpCoreTS event log 10 October 2021 05:52:44 AM: No Failure Audit Events found in Application event log 10 October 2021 05:52:44 AM: Source IP summary (Top 10): 10 October 2021 05:52:44 AM: IPAddress : 94.232.47.56 ReverseDNS : IPLocation : Moscow, Moscow, 127224 - RU (55.7522,37.6156) IPOrg : AS204490 Kontel LLC IPTimeZone : Europe/Moscow AttemptCount : 1045 Percent : 47.94 % IPAddress : 94.232.47.57 ReverseDNS : IPLocation : Moscow, Moscow, 127224 - RU (55.7522,37.6156) IPOrg : AS204490 Kontel LLC IPTimeZone : Europe/Moscow AttemptCount : 1038 Percent : 47.61 % IPAddress : 193.93.62.80 ReverseDNS : IPLocation : Riga, Riga, LV-1001 - LV (56.9460,24.1059) IPOrg : AS39814 SIA IT Services IPTimeZone : Europe/Riga AttemptCount : 45 Percent : 2.06 % IPAddress : 193.93.62.72 ReverseDNS : IPLocation : IPOrg : IPTimeZone : AttemptCount : 37 Percent : 1.70 % IPAddress : 193.93.62.84 ReverseDNS : IPLocation : IPOrg : IPTimeZone : AttemptCount : 15 Percent : 0.69 % 10 October 2021 05:52:44 AM: Source IP summary exported to .\Reports\Summarize-FailureAudit_PerSourceIP_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:44 AM: Logon Attempt Type summary (Top 10): 10 October 2021 05:52:44 AM: LogonType AttemptCount Percent --------- ------------ ------- Network 2180 100.00 % 10 October 2021 05:52:44 AM: Logon Type summary exported to .\Reports\Summarize-FailureAudit_PerLogonType_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:45 AM: Attempted Account summary (Top 10): 10 October 2021 05:52:45 AM: Account AttemptCount Percent ------- ------------ ------- Not reported in event 140 137 6.28 % \ADMINISTRATOR 90 4.13 % \energyprz 1 0.05 % \drkulas 1 0.05 % \fontaine 1 0.05 % \dreamlines 1 0.05 % \fatlab 1 0.05 % \docuprint 1 0.05 % \g2is 1 0.05 % \energychaser 1 0.05 % 10 October 2021 05:52:46 AM: User Name summary exported to .\Reports\Summarize-FailureAudit_PerUserName_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:46 AM: All records exported to .\Reports\Summarize-FailureAudit_All_10October2021_05-52-43_AM.CSV 10 October 2021 05:52:46 AM: Latest 10 attempts: 10 October 2021 05:52:46 AM: EventID ComputerName LogName Account SourceIP TimeCreated ------- ------------ ------- ------- -------- ----------- 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:20 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:20 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:18 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:17 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:16 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:16 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:14 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:13 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.57 10/10/2021 5:52:12 AM 140 mycomp1.mydomain.com Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational Not reported in event 140 94.232.47.56 10/10/2021 5:52:11 AM
This log file and numerous similar logs show:
- Incoming attempts; mostly from Russia; to guess (mostly) ‘Administrator’ account password on Windows computers that are listening for RDP (Remote Desktop Protocol) connections.
- The attackers’ automation is able to recognize which of their sender nodes are blocked and use other unblocked nodes to continue the same attack.
- The Windows firewall rules can block a maximum of 10k IPs/CIDR subnets per rule.
So if the Block-FailedLogonIPs PowerShell automation is scheduled hourly, it detects and blocks the attacker IPs for the prior hour. However, the next hour IPs are different. The attacker does not seem to run out of IPs, or to have a Botnet with larger than 10k nodes. This solution essentially fails at its intended purpose of blocking unauthorized RDP connections. It, however, has the unanticipated side result of building a database of thousands of the attacker IPs.
This new function Block-IPsPerCountry takes a different approach to the same problem. It leverages GeoIP information (courtesy of ipdeny.com) to create firewall rules to block all incoming IP traffic except a given 1 or more countries.
Example:
$RuleSet = Block-IPsPerCountry -AllowCountry @('us','gb')
This may take several minutes to complete. This example blocks all incoming IPv4 traffic except from USA or Great Britain. Console output looks like:
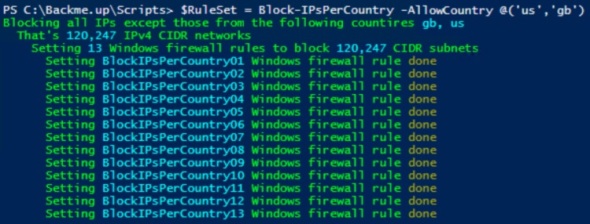
ISO Alpha-2 country code list can be seen here.
Continuing to use Block-FailedLogonIPs PowerShell automation as an hourly scheduled task shows no more incoming attempts to crack Administrator password via repeated RDP logon attempts.
To use/update the AZSBTools PowerShell module which is available in the PowerShell Gallery, you can use the following code:
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
# PowerShellGallery dropped Ssl3 and Tls as of 1 April 2020
Remove-Module AZSBTools -Force -EA 0
Install-Module AZSBTools -Force -AllowClobber -SkipPublisherCheck # -Scope CurrentUser
Import-Module AZSBTools -DisableNameChecking -Force
Get-Command -Module AZSBTools
You need PowerShell 5. To view your PowerShell version, in an elevated PowerShell ISE window type
$PSVersionTable
To download and install the latest version of AZSBTools from the PowerShell Gallery and its dependencies, type
Set-PSRepository -Name PSGallery -InstallationPolicy Trusted
To trust the Microsoft PowerShell Gallery repository, then
Install-Module AZSBTools,Az -Force -AllowClobber -Scope CurrentUser
AZSBTools contains functions that depend on Az module, and they’re typically installed together.
To load the AZSBTools, and Az modules type:
Import-Module AZSBTools,Az -DisableNameChecking
To view a list of cmdlets/functions in AZSBTools, type
Get-Command -Module AZSBTools
To view the built-in help of one of the AZSBTools functions/cmdlets, type
help <function/cmdlet name> -show
such as
help Get-DayOfMonth -show
Upgrading Server 2012 R2 to Server 2016 and Storage Spaces
Server 2016 has enhanced and added new features to Storage Spaces. Most notably is the introduction of Storage Spaces Direct, Storage Replica, and Storage QoS. This post explores upgrading a physical Server 2012 R2 that uses mirrored tiered storage space.
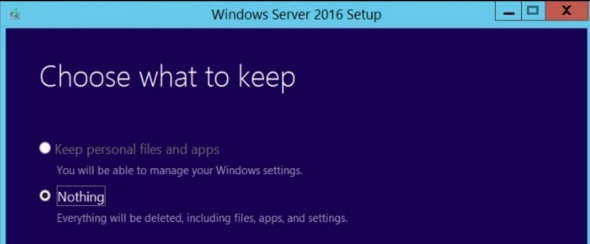
After installing Server 2016 (Desktop Experience), and choosing to keep ‘nothing’
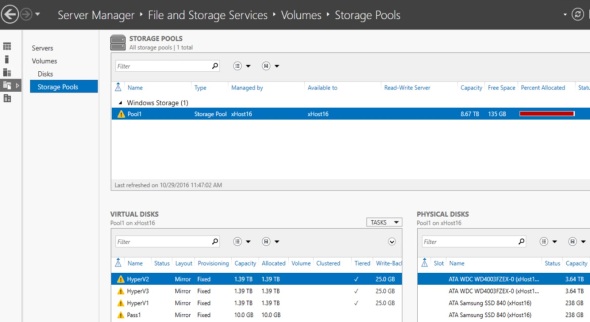
In Server Manager, File and Storage Services\Volumes\Storage Pools, we see the old Storage Pool from the prior installation of Server 2012 R2
To recover the Storage Pool, its virtual disks, and all data follow these steps:
- Set Read-Write access

- Upgrade the Storage Pool Version
 Note that this step is irreversible
Note that this step is irreversible

- Right click on each virtual disk and attach it

- Finally, in Disk Management, right click on each virtual disk and online it

The virtual disks retain the drive letters and volume labels assigned to them in the old 2012 R2 server. All data is intact.
Upgrading Server 2012 R2 to Server 2016
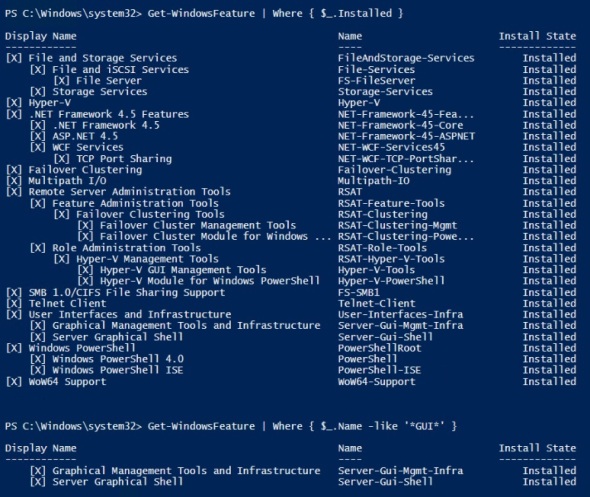
Server 2016 migration guides are not available yet (26 October 2016).  So this post will explore a domain joined physical Server 2012 R2 to Server 2016 upgrade. This is from Data Center to Data Center edition. The 2012 R2 server has the following roles:
So this post will explore a domain joined physical Server 2012 R2 to Server 2016 upgrade. This is from Data Center to Data Center edition. The 2012 R2 server has the following roles:
First I mounted the image:
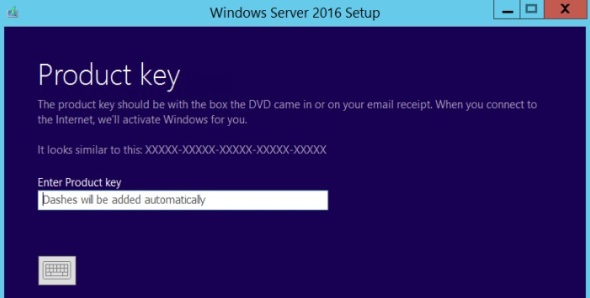
Being a Hyper-V host, I live-migrate the production VMs to other Hyper-V hosts. All other VMs are shutdown. Then I run the setup.exe
and download the latest updates, enter the product key
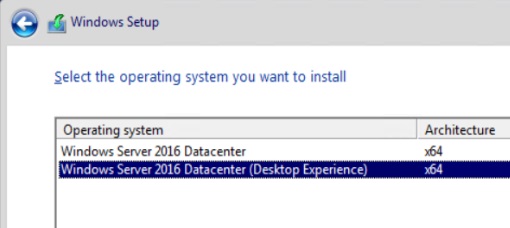
Depending on the product key you enter, the next screen shows the corresponding Windows Server edition. I select Data Center (Desktop Experience). This is the option that provides a GUI. For more information on Server 2016 GUI options see this post.
accept license terms, and attempt to select to keep personal files and apps (not default option)
Issue with Windows Edition and keeping personal files and apps:
However, that option is not available – un-clickable. The message at the bottom complains about different Windows Editions. That’s not true. As you can see in the background, a PowerShell command that indicates that this server is running 2012 R2 Data Center Edition 😦
I will proceed here since there’s really no personal files or apps that I need.
When you try to proceed, you get a confirmation message that refers to Windows 10 !!??
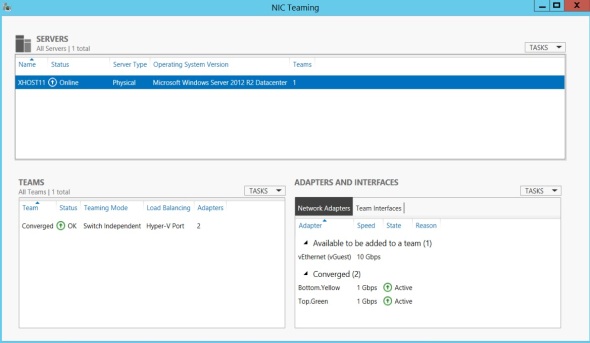
This server has a NIC team configured as follows:
There’s a single external vSwitch bound to the NIC team with a vNIC for the parent partition
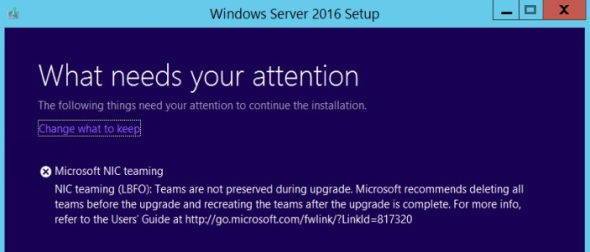
NIC teaming is not supported during upgrade:
Now breaking the team, means this upgrade cannot be done over an RDP session. To do it remotely you need console/baseboard access. Most modern servers like Dell, HP, and UCS do.
It then proceeds to download the updates:
Again references to Windows 10 in the middle of Server 2016 installation/upgrade
Moving on
Next we get full blue installation screen